Through this access, clients can open, read and edit the shared documents, which are automatically saved on the local machines. Users can also access interprocess communication services and print queues. CIFS was developed in the early 1980s at IBM.
How CIFS works
CIFS follows a client-server model. Three entities are involved; a client, an application, and the server.
The client implements the protocol where most of the messages originate. The server implements the protocol and provides most of the functionality (service). The application can be a piece of software that performs functions such as graphic user interface, file management, or word processing.
This is how CIFS works;
A NetBIOS session to access the shared resources is established between the client and the server. The negotiation process is where the client and the server determine the dialect that will be used. The client submits the authentication credentials, mostly a username and password, to the server through a unique identifier. Active Directory mostly handles the authentication process. However, CIFS does not handle authentication directly. The server returns the unique identifier if the authentication is successful. The server checks if the client has the required permissions and if the share name is valid. If all these details are valid, the client is granted access to share resources such as files and folders.
CIFS Protocol Features
Transport independence
CIFS protocol does not place any requirement on the transport protocol that sends SMB messages between the server and the client. CIFS is simply carried over a connection-oriented protocol.
File access
A client/user can open, read, modify and close multiple files on a target server. The server is tasked with file sharing, meaning multiple clients can open and read the same file simultaneously and on different devices.
Has file, directory, and volume attributes
CIFS protocol can query and also, with limited capability, set directory, file, and volume attributes. Access Control Lists (ACLs) are also supported on CIFS.
Extended subprotocols
CIFS protocol supports various subprotocols that offer direct access to additional server functionality.
Supports named pipe interprocess communication
The client can open, write, read and close named pipes on the specific server. Named pipes offer a communications path between the server and client services.
Flexible connectivity
One client can connect to multiple servers. Such a client can also make one or more connections to a server.
Supports feature negotiation
A protocol’s supported feature set and dialect are negotiated per-connection basis.
File and record locking and safe caching
CIFS protocol support record and file locking. The same protocol allows for opportunistic file locking, granting clients the opportunity to cache data for better performance.
Directory and file change notifications
Clients on the CIFS protocol can post a request to be notified whenever a change is made within a resource, such as a file within a directory or a directory on a specific server.
Supports Distributed File System (DFS)
DFS creates a global namespace containing resources on multiple servers.
Supports multiple security contexts
A client can use and create one or more security contexts over a certain connection.
Preconditions to use CIFS
CIFS needs an underlying network transport (generally connection-oriented). However, in some cases, CIFS messages can be transmitted through connectionless transport with some minor modifications. Before CIFS messages can be exchanged over a connection-oriented transport, a connection must be established. For messages to be exchanged over such a network, CIFS will assume that one or more of the following resources are available;
A local print queue that sends print jobs to a printer to offer print services. A local file system or database is presented as a file system to enable file sharing. The resource, in this case, is known as an object store. A suitable emulation built into the CIFS server or a file system that supports named pipes is needed for interprocess communications using the named pipe abstraction.
The server should also have or provide access to a password database for authentication. The password database stores the NT LAN Manager (NTLM) and LAN Manager (LM) password hashes to support challenge or response authentication.
Configure CIFS for Windows
Most users will never use CIFS, which explains why the feature is disabled by default on Windows 10 and 11. Follow these steps to get it working;
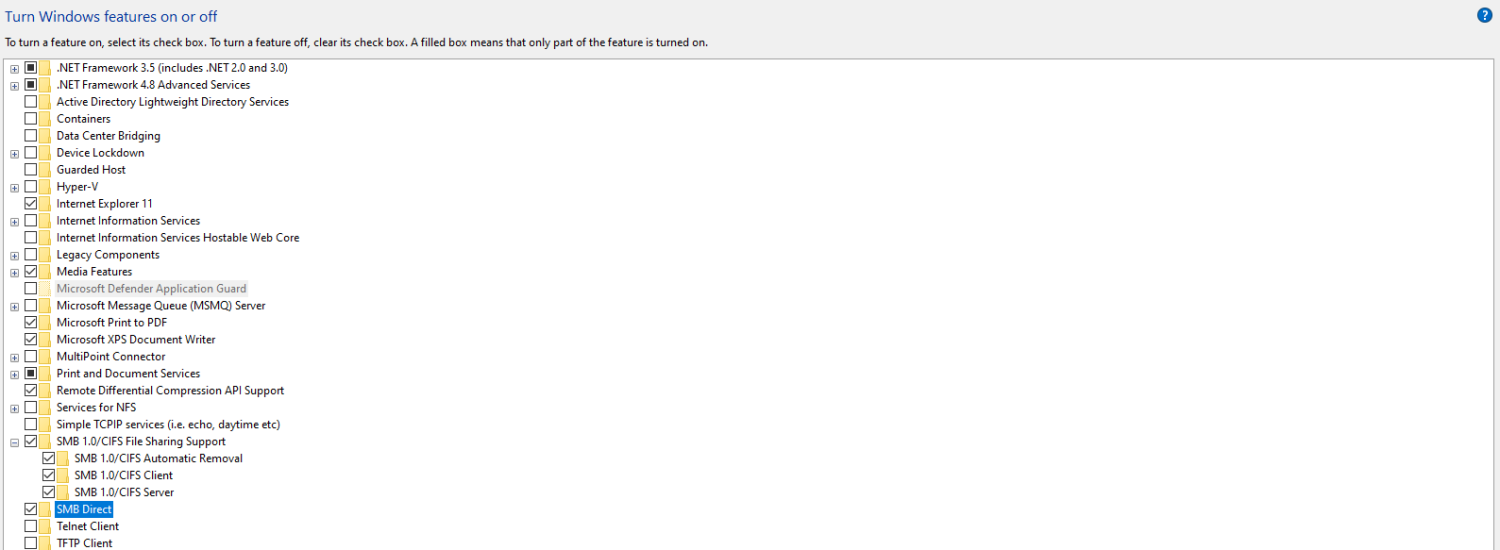
Go to the Control Panel and click on Program and Features. On the left-hand side, click on Turn Windows features on or off.
Scroll down until you see SMB 1.0/CIFS File Sharing Support and tick that box. Click on the + icon to see all the checked options
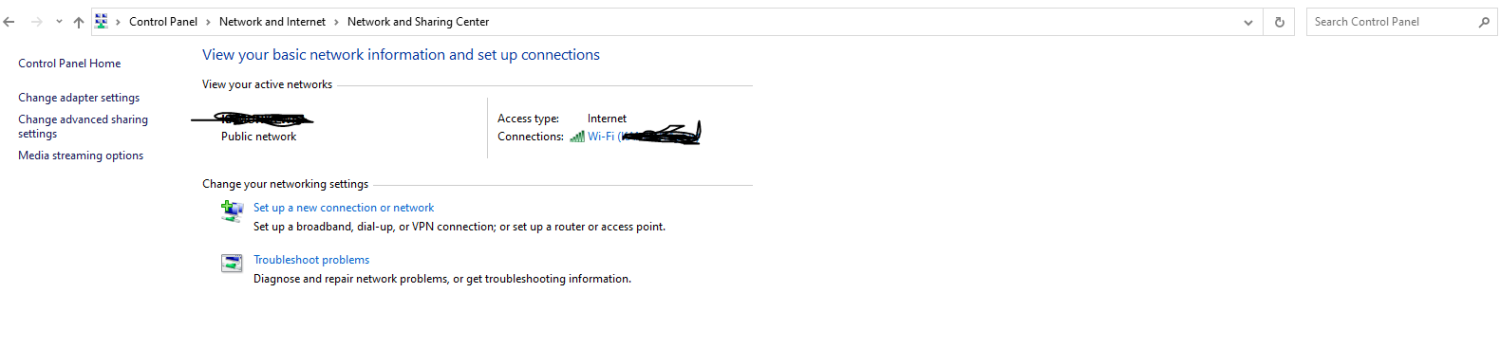
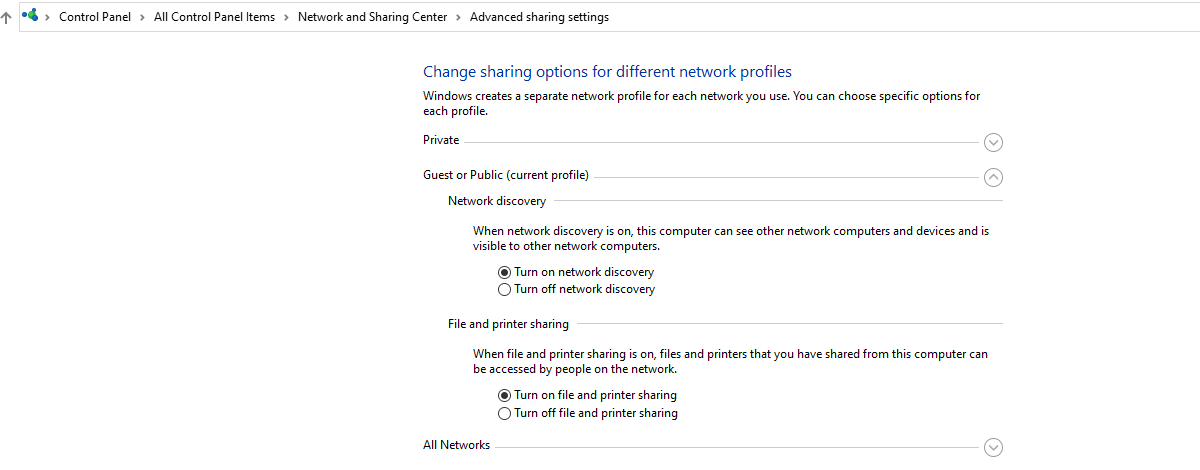
The above steps will turn CIFS on. However, you need to configure the network you are connected to for CIFS. This is the process; 2. Click on Network and Sharing Center. On the left, click on Change advanced sharing settings. 3. Click on Change advanced sharing settings. You can now go ahead and Turn on network discovery and Turn on file and printer sharing. Click ‘save changes’.
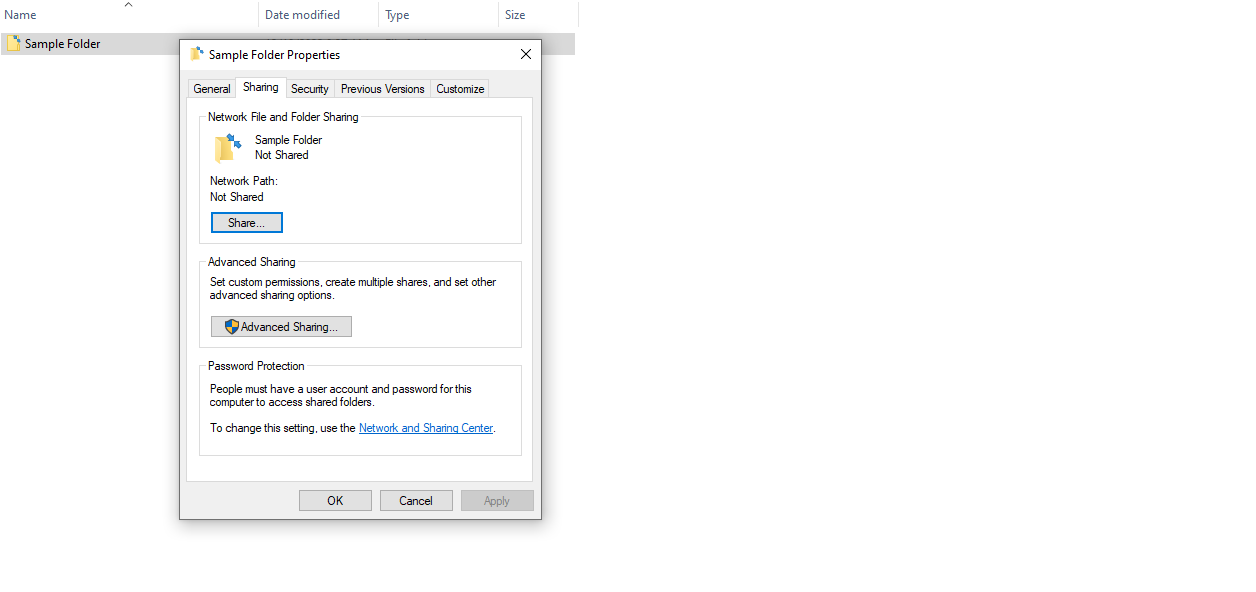
Setup CIFS on a Folder
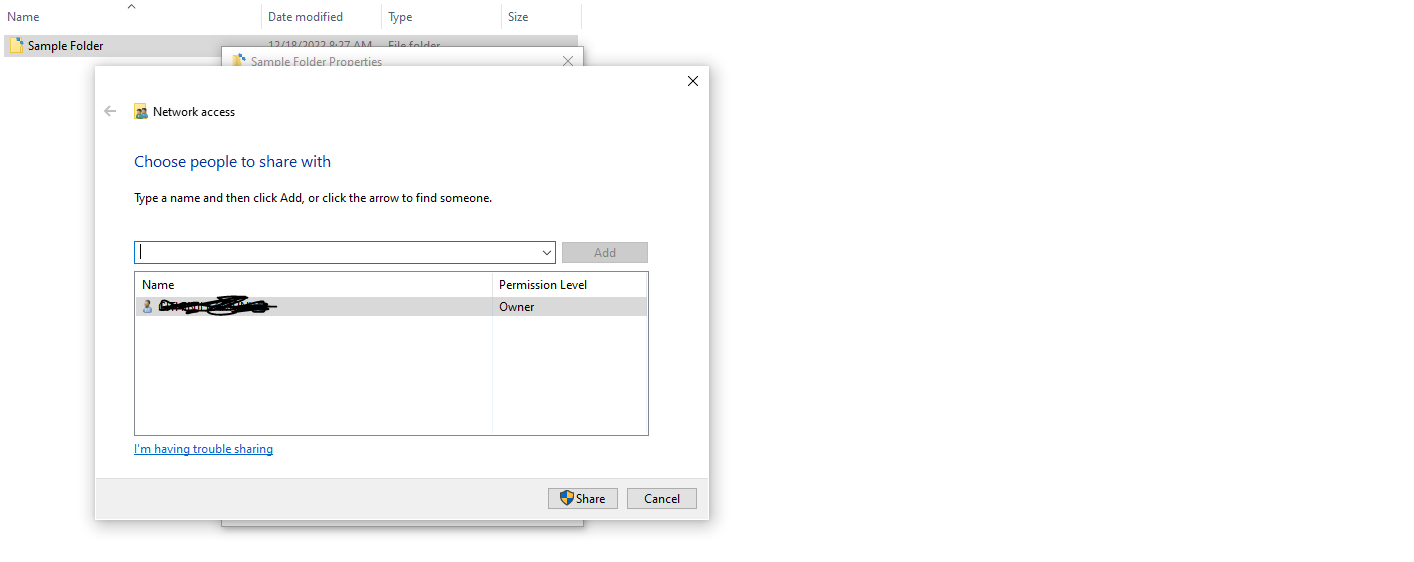
For the purposes of this demonstration, we will set up a folder called “Sample Folder” on Disk E. 2. Click Share. However, you must note that the listed users are only those currently set up on your Windows machine. The recipients must also configure everything on their side if they want to access the sent documents.
CIFS vs. SMB: Differences
Before checking on the differences, it was worth learning what Server Message Block (SMB) is. Server Message Block was designed to allow a client read, write and edit a file in a server. The server, in this case, is a Local Area Network (LAN).
SMB over the years
SMB 1.0. The first version of SMB is equated to CIFS. This first variation was created for Windows NT 4.0 and communication was over NetBIOS interface. SMB 2.0. This version was introduced by Microsoft in 2006 through its Windows Vista operating system. Some of the features introduced were better scalability, support of symbolic links, and improved message signing. SMB 2.1. This version was introduced at the same time as Windows 7 in 2007. Version 2.1 offered improved performance optimizations and new locking mechanisms. SMB 3.0. This version was introduced at the same time as Windows 8 in 2012. SMB 3.0 was originally named SMB 2.2 but was renamed later. This version created the possibility of remote storage access through Remote Direct Memory Access (RDMA). SMB 3.1.1. This is the latest version as of this writing. SMB 3.1.1 was created for Windows 10 in 2015 and introduced integrity checks before authentication. This version also utilizes encryption with Galois/Counter Mode (GCM).
Many people confuse CIFS and SMB. It is worth noting that SMB was introduced earlier than CIFS. Microsoft improved on SMB to create CIFS in the 1990s, which makes CIFS a dialect of SMB. However, Microsoft has continued to improve CIFS, and the current version is SMB 3.1.1. These are the major differences between the CIFS and SMB 3.1.1
What are the downsides of CIFS?
Lacks authentication. One of the biggest downsides of CIFS is that it lacks authentication, unlike the latter versions of SMB. Handles limited file sizes. CIFS may not be ideal for super large files, causing delays and may even cause breakages during transfer.
Conclusion
Although cloud file sharing and access services seem to be taking over, traditional protocols like CIFS still have their space. Support for direct connections over TCP port 445 was one of the biggest selling points for the CIFS. Even though Microsoft is now focusing on progressing SMB, CIFS cannot be forgotten as it is one of the SMB dialects. You may also explore how to run system file checker in Windows 11/10.

![]()